This Forum is now live!
Feel free to use it as a way to discuss and submit feedback regarding the different services hosted on Tiekoetter.com
You can also chat with like-minded people!
This Forum is now live!
Feel free to use it as a way to discuss and submit feedback regarding the different services hosted on Tiekoetter.com
You can also chat with like-minded people!
Let's start chatting 
Regarding Invidious: YouTube is currently A/B testing disabling DASH. Invidious uses DASH for the video streams. YouTube wants their in-house protocol, SABR, to be the new default. Some mitigations are now in place to get DASH back but consider Invidious unstable for the foreseeable future as YouTube will likely disable them sooner or later as well.
Hello,
please post your feedback / issues / comments regarding IPv6 access via AS208694 (www.as.tiekoetter.net)
I would appreciate your input to evaluate the functionality of AS208694 for future adjustments.
That is a good question and I was looking at Discourse initially but couldn't get it to work how I would have wanted. It also throws countless errors and seems more hacked together than a thought through software. The docker image was not really working, this may also be an error on my part but they officially don't support docker as an install method which I thought was a red flag.
I came across NodeBB in my research for a modern forum software. Looked promising. They provided a clean docker install method. I also noticed that Netgate (the company behind pfSense) uses NodeBB for their forums.
It also looked easy to maintain, which turned out true, so I settled on it.
The Nitter instance is currently degraded as the accounts used in the back-end are rate limited. This is, from what I can view, due to legitimate requests.
Meaning I have to add new accounts, which takes a bit of time.
I have upped the Anubis difficulty from 4 to 5 in the meantime.
Yeah the status page is just checking if the index responds with 200 or at all. I could check specific paths but I cache most of it.
The reason why it behaves like this is because my instances gets hammered with 5 times the usual traffic for almost the last 72 hours.
Looks like legitimate traffic.
I would have to add more twitter accounts as the current number always sits limited at 95-98% which gives you the "rate limited" error message. If you refresh a few times you may get through to a valid session.
I will have to monitor this for the next few days. Adding more twitter accounts is very tedious.
Thanks for voicing your concerns!
You can change this on under your profile -> settings. There you can change each different notification type from "notification only" to "notification & email". I have this set to notification only so it doesn't spam inboxes by default.
Hope this helps and thanks for your feedback!
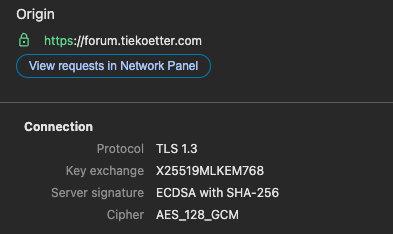
More specifically the "X25519MLKEM768" group if the client supports it. Fallback are still the normal "X25519" and "SecP384r1" groups if the client doesn't support the MLKEM group.
Why is this important?
Quantum computing could break standard cryptography when it matures. These Module-Lattice (ML) Key Encapsulation Methods (KEM) are designed to withstand future quantum computing attacks.
What does "X25519MLKEM768" do?
As the name might suggest it combines both mechanisms of "X25519" and "ML-KEM-768" forcing an attacker to break both mechanisms to break the cryptographic key exchange.
Drawbacks?
As this is using both the standard "X25519" mechanism and the "ML-KEM-768" encapsulation mechanism it is more computationally expensive as the "X25519" standalone. This should be negligible on modern systems.
You can check if your Browser supports this by opening the browser console and selecting the security tab. Something like this should be shown:
I guess Wikipedia has finally decided to block my Server.
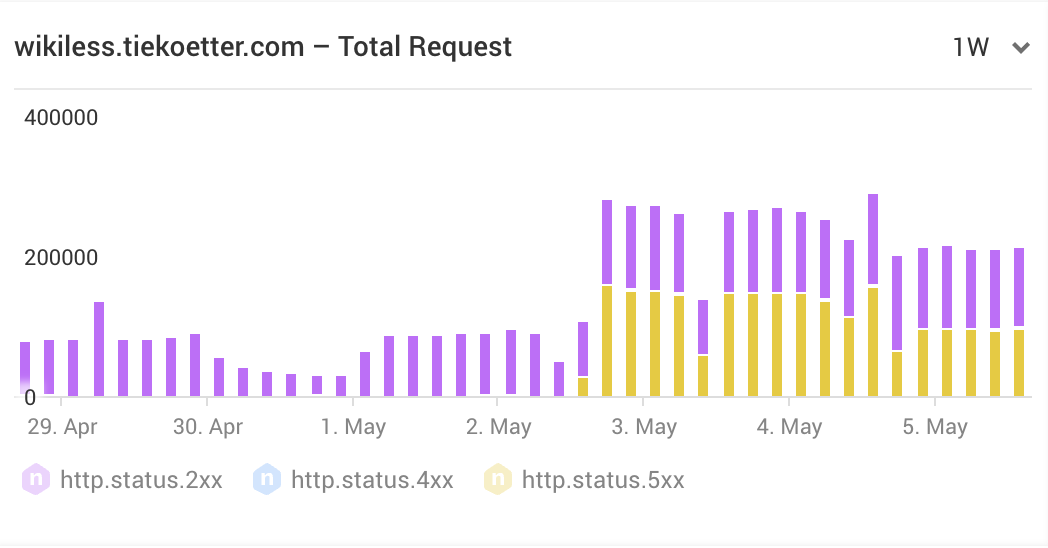
The back-end reports 429 from the wikipedia.org servers.
Currently Wikiless doesn't support proxy servers. I would have to fork Wikiless and implement it myself for it use my proxy back-end. I may have to look into this in the future.
I have implemented IPv6 access via AS208694 for searx.tiekoetter.com, invidious.tiekoetter.com, wikiless.tiekoetter.com and this Forum.
AS208694 is operated by me and serves as another layer of control. Currently only IPv6 is possible as IPv4 is far too expensive for an individual to get. The IPv6 access is terminated at the same server, it is just routed differently. It works in conjunction with the current IPv6. I may expand this to the other services in the future.
More information about AS208694 can be found here: www.as.tiekoetter.net
The Nitter instance is now fully restored again.
It looks like Nitter got nuked.
https://status.d420.de/
My instance only has cached results available. I will have to take a look later today.
Just checked it. It was actually Twitter that was down and not the Nitter instances. It is still a bit flaky but so is Twitter itself right now.